Because it is not as vulnerable as many have hoped, MacOS attackers are now looking to use techniques that worked well on Windows a few years ago. The new ways that are being exploited to infect and spread malware on MacOS are already well known in Windows and have been highly successful thanks to the inattentiveness and ease of use of the users. The recent findings prove this and two new malware are circulating, seeking to exploit flaws that are external to MacOS, but that end up compromising this operating system.
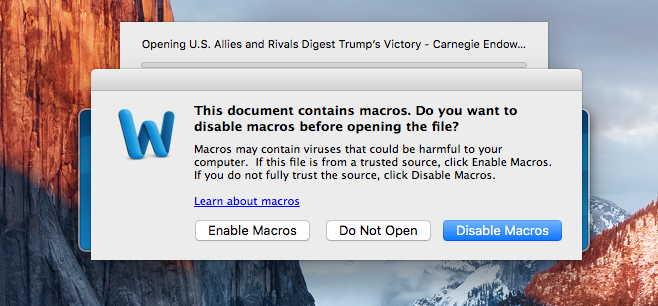
The old Word macros trick in MacOS
The first form of infection was discovered by the company Objective-See and exploits a known bug in Windows, Word macros. Several files with hidden code go around and infect users of MacOS. But, just like in Windows, this form of infection has flaws. When a file with this code is opened, an alert is displayed to the user, who must authorize the macros to be executed. The problem only happens when they are authorized, leading to other malicious software being installed or data being stolen from the users. The second known form of attack was revealed by researchers at Iran Threats, and it is a bit more advanced. It uses seemingly normal applications as an attack vector and leads users to install other applications in the hope of making MacOS better. Also, this attack is well known from Windows and has been used for many years. These applications later lead to the stealing of user data and its sending to attackers. All these attacks and forms of infection are nothing new. They have been used for many years in Windows, and still today they can fool users. So, this move to MacOS shows that there is a renewed interest in this platform, which has more and more users.